"Openly Operated wants to make privacy policies actually mean something... [it] lays out an attractive paradigm for privacy."
What is Openly Operated?
Trust Through Transparency
The Transparency Certification For Apps
Openly Operated is a certification given to apps that operate with full transparency. To receive it, the app goes through the certification process and provides public proof of its privacy and security claims, as well as its comprehensive audit results. Openly Operated enables a level of trust not possible with today's typical black box app, where users have no idea what's really happening with their data.
Instead of just publishing a Privacy Policy, Openly Operated apps are able to prove their privacy claims with their public Audit Kit and Audit Reports. This page describes Openly Operated in the context of VPNs, and we encourage you to further learn about the Openly Operated certification and how it provides the verifiable transparency that products desperately need today.
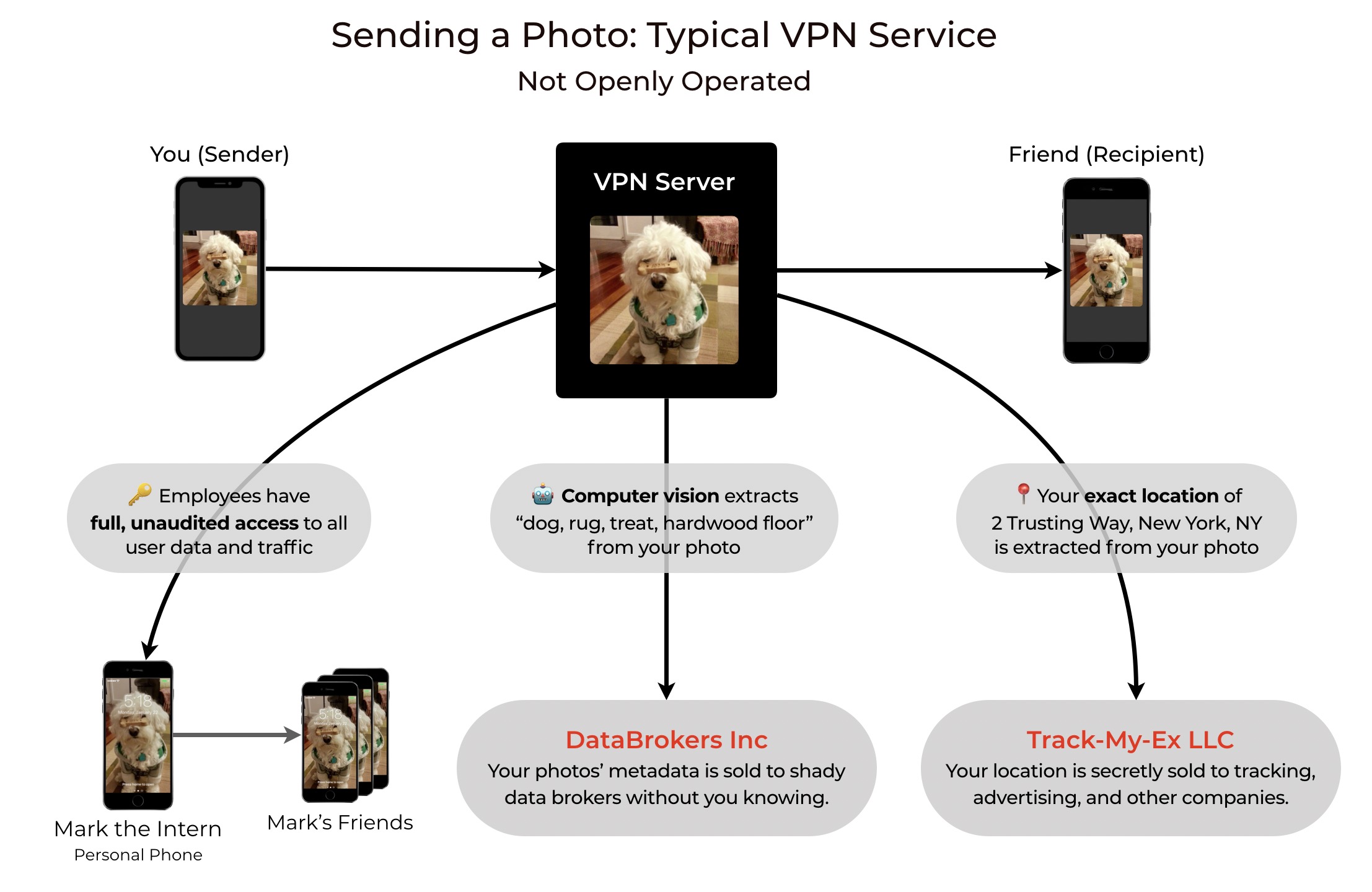
Apps Today Are Black Boxes With No Accountability
Ever wonder why VPNs are so often "85% off!" or even completely free? It's because they're selling your data and metadata to brokers and third parties. And since you send all your data through the VPN, the VPN company has access to pretty much everything you do. And their Privacy Policy doesn't help, because they simply lie on it since there's no real enforcement of Privacy Policies, especially for companies that are headquartered offshore, outside of any consumer protection laws. Apps today have no transparency, so using a typical VPN can be quite dangerous:
Openly Operated Creates Trust Through Transparency
Openly Operated requires companies to be completely transparent through five major requirements: Open Source, Open Infrastructure, Identify Operation, Establish Provenance, and Audit Trail. These requirements are fulfilled by the company and packaged into a public Audit Kit, and then independent Auditors verify each part of the Audit Kit and publish Audit Reports detailing their findings.
By completing the certification process, companies have to not only open source all code, but also open up all operational aspects of their service, leaving no room for the service to hide software that might be selling your data to third parties, or improperly protecting data from company employees and other threats. See the difference:
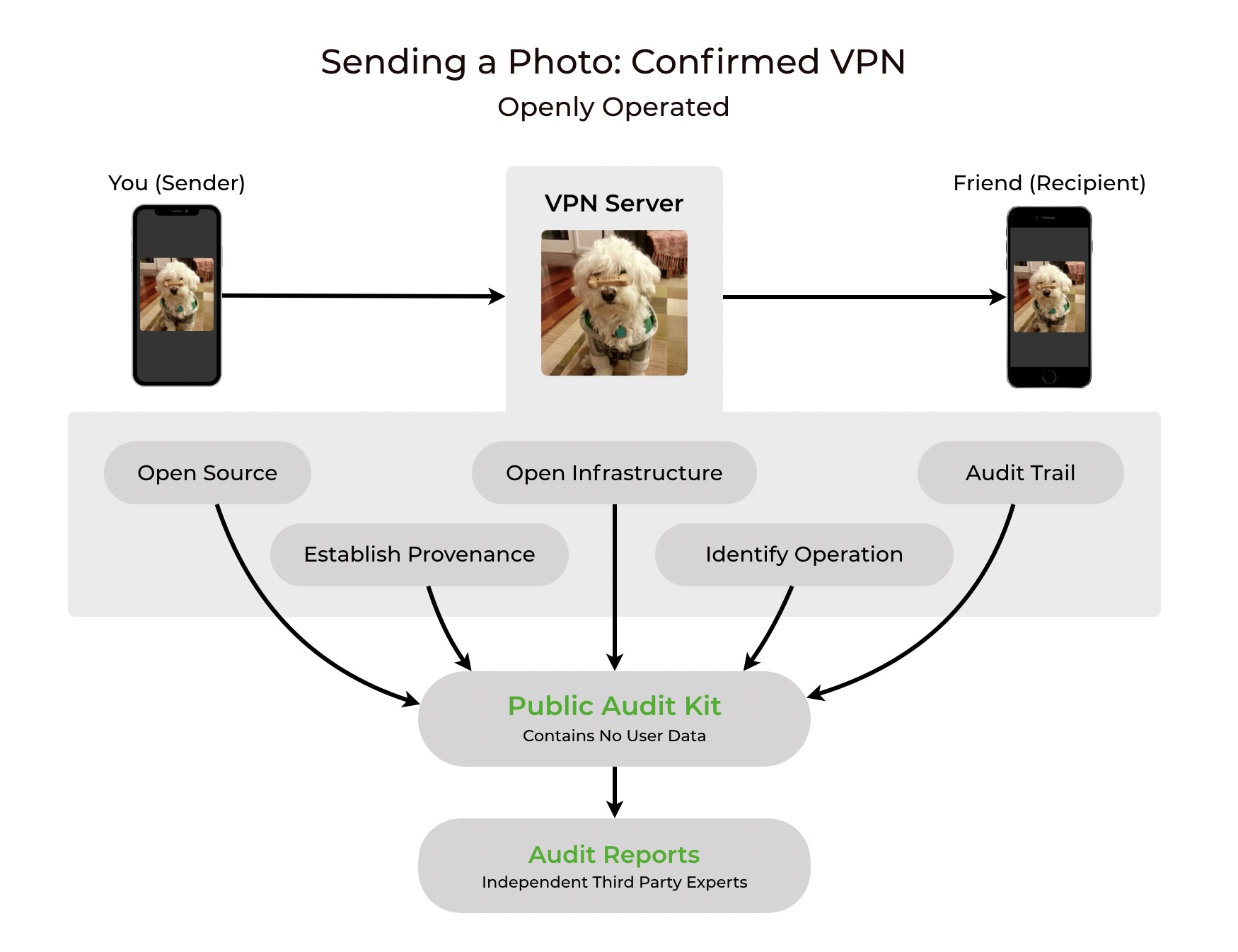
The First Openly Operated VPN
When we came up with Openly Operated standards, we wanted to prove that it could work by building a real product. We picked the industry most vulnerable to abuse of customer data: VPNs. When you activate a VPN, all your data and browsing passes through it, so it's especially important that you can trust your VPN.
Confirmed VPN's public Audit Kit and Audit Reports are available below. Whether you're a user, a developer interested in earning user trust, a security or privacy professional, or just plain curious, we hope you have a chance to read about how the Openly Operated certification works and help spread the word about the need for companies to provide users trust through full, verifiable transparency.
Our Mission
At Confirmed, our mission is to increase user trust in the web services and apps that they use every day. People shouldn't have to be in the dark about what's happening with their personal data. We believe that complete transparency through being Openly Operated is the future, and that once people experience this level of trust and assurance, they'll never want to go back to black box apps again. Learn more About Us or about Openly Operated.
Start a free 1 week trial.
Try the only Openly Operated way to browse securely and privately.
DOWNLOAD
Mac iOS PC Android
